What If It Was A Software Bug/Virus? Cyber vs. COVID-19: A Thought Experiment

The metaphor of software viruses to biological ones is deeply ingrained, easily seen in the fact that biological viruses are at least the namesake, if not the inspiration for computer viruses.
Can we take this analogy and reapply it in reverse? Is it possible to learn more about how we can combat biological viruses, such as the raging COVID-19 epidemic, by leveraging concepts, mindsets, and ideas that evolved in the software engineering and cybersecurity worlds? This is what we’re going to try and explore in this thought experiment, with the purpose of creating discussions that may fuel better understanding and perhaps even new solutions.
Completing the analogy
The world of software is a complex one and the world of biology (coming in with an unfair advantage of about 4 billion years head start 😀 ) makes the complexity of software look like a joke. With such complex realms it’s difficult to satisfy the thought process by simply saying that a virus is analogous to a virus. Rather, we have to go much deeper. While there are probably many ways to draw this analogy, by picking some semantics we’d be better off than deciding on none. In addition, we will focus the analogy to best suit the characteristics of COVID-19 (as compared to other pathogens, viruses, and bacteria).
Analogy points
- Vulnerability – A defect in a mechanism that allows the mechanism to operate in a way it wasn’t intended to. It is the same for both sides of the analogy. A cyber example would be a vulnerability in the OS code that reads a USB stick’s filesystem, which causes a specifically crafted USB drive to run malicious code on the system without the user’s intention. A biological example would be a virus code that is injected into a cell, which causes the cell to execute the code as if it was its own.
- Executable
- Software: a binary or script file
- Biology: a strand of DNA or RNA
- Code-execution
- Software: A binary/script file being loaded/run by a process
- Biology: mRNA being translated into peptide chains by a Ribosome
- Infected Node
- Software: a network node such as a laptop or server
- Biology: a cell
Connected entity:
- Software: Sub Network / VLAN
- Biology: Living tissue or organism
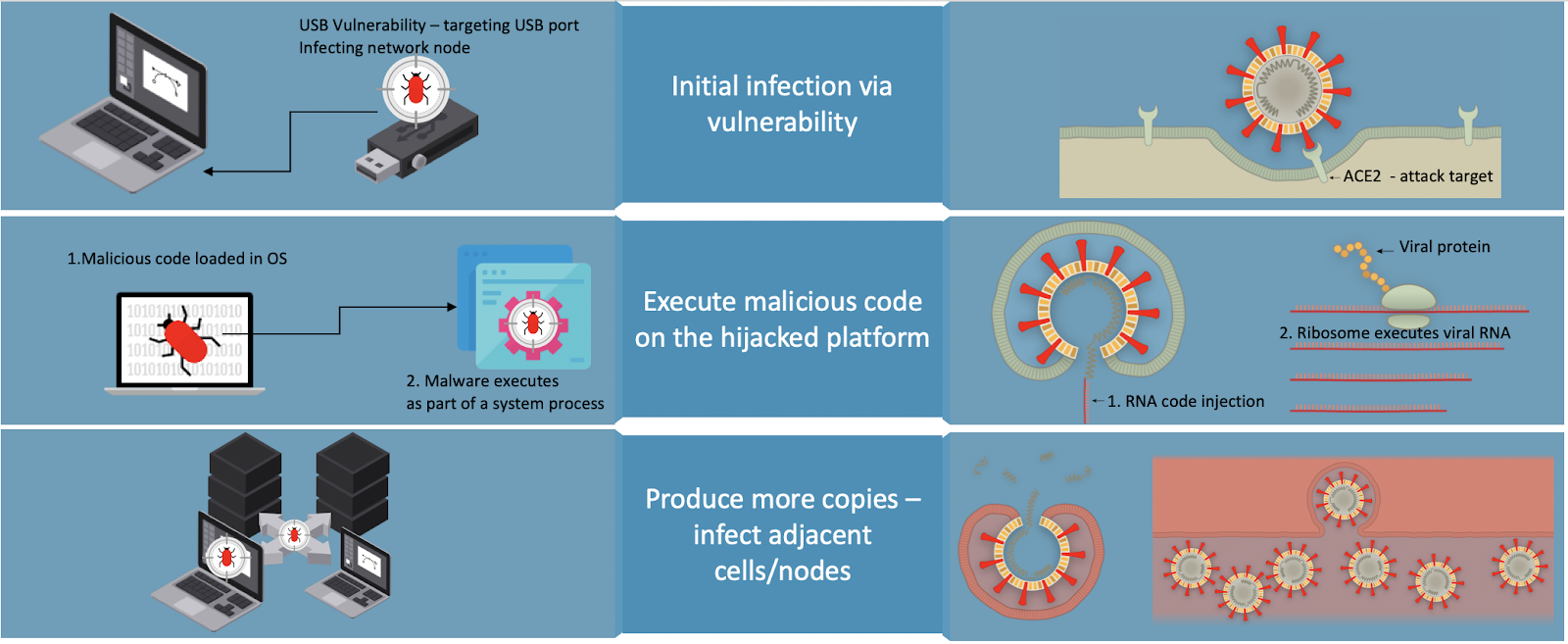
Attack analogy diagram / With graphics from Nytimes.com – “How coronavirus hijacks your cells”
It’s important to note that while we have a rather good understanding of software and cybersecurity (though even there much remains to be explored), the world of biology still remains more of a mystery for us in comparison. This is probably a direct result of our having designed and created the software world, but we didn’t design or create the biological one (it actually created us). This gap of understanding, and applicable technology – makes some – if not most – of the solutions we have in the software realm harder to implement in the biological one.
Now that we have both the analogy and expectations set in place, let’s take a look at analogs solutions that already exist and then move to cybersec solutions we can use to derive new biological/medicinal capabilities by analogy.
Solutions that exist (at least partially) in both worlds
- Antivirus pattern matching: Antibodies in the immune system
Just like antivirus software often relies on malicious code/file signatures to identify and thwart malware, so too does our immune system produce signatures on viruses via memory cells (e.g. T-cells and B-Cells). A big difference remains in how signature updates are acquired. Vaccines are an indirect way to cause the immune system to acquire a new antigen signature. Imagine if your immune system could, like your AV software, download an update from the web or even from a local service. - Code sanitization: CRISPR / CAS9
Code and data sanitization are very common in software, as a leading way to protect against code injection. While we haven’t been able to significantly harness CRISPR yet, the mechanism has been utilized by bacteria for eons for defence against viral DNA. This enables said bacteria to remember virus DNA and cut it out of sequences to avoid it’s activation. We (humans) are already using CRISPR today in vitro (and in vivo use is just around the corner). - Code Packers: Cell Nucleus, Chromosomes, DNA
Code packers protect an executable from intervention and manipulation. The cell nucleus adds an additional layer of protection within the cell. While chromosomes act as archives, DNA’s double helix provides redundancy on the data and enables error correction (like checksums). In the software space these often include compression and encryption– I sincerely hope that viruses don’t evolve to adapt those to trick the immune system. - Endpoint Firewall: breathing masks
An endpoint firewall (also known as a personal firewall), protects a network node from attacks by limiting the type or content of traffic – minimizing the attack surface. A simple parallel found in the healthcare world is face masks. We can consider more complex filtering mechanisms (such as smart-masks or smart suits) which, like a network firewall, would be more configurable to adjust to specific threats and needs. If the epidemic continues to rage, this would probably be a leading category for IoT and wearables to grow into.
Solutions we can import from cyber to the biological world
- Honeypot – A cybersec method using deception and fake assets to both detect attackers and interfere with their process. Viruses like COVID-19 target specific cells (in COVID-19’s case it targets cells that have the ACE2 enzyme on their cell membranes). Possibly by producing fake cells (be they cell simulations, or actual engineered cells [e.g. bacteria]) with the enzyme we can both create alarms for the existence of the virus, as well as waste some of the viruses’ resources on infecting these fake cells.
This technique actually seems to be right at the edge of our current scientific capabilities. By imagining combining bacteria, plant, or even animal cells with bioluminescence triggered by the viruses code (RNA), we can have elements around us or even the air itself light up as a warning sign for the presence of the pathogen, which should make detection, testing, and even containment far easier. - Execution protection
The core vulnerability that viruses exploit is unprotected and unprivileged code execution, as basically any strand of RNA or DNA which finds its way into the inside of a cell gets executed. This concept is so alien to modern software architecture, basically making it sound absurd.
Let’s look at several of the solutions found in cybersec and how we can conceptually apply them to biology:
- NX bit – Modern CPUs support marking specific areas in memory as executable or not and hence restrict execution to only approved code. What if we could make sure only human DNA is marked for execution, by say adjusting the cell’s mechanisms to check for approved signatures or lack thereof, and either not execute or proactively reject mismatches? This technique requires updating the underlying cell architecture (as it did for CPUs) and is probably far beyond our current technological grasp, but it does enable us to imagine a future where we evolve a subspecies of engineered humans who are essentially immune to all existing (and probably most future) viruses.
- Execution privilege levels – Different executables/processes have different execution rights and modes (e.g. kernel mode, user mode). What if we could limit specific cells to only perform specific operations- i.e. execute only specific DNA/RNA? While basically all cells with a nucleus in the human body (aside from gametes) contain all the DNA, cells don’t actually need or use all of it. Thus conceptually we could limit specific cells to be allowed to execute only the code they actually need. This method -unlike the full architecture change described above- can be applied in a more limited scope. For example, targeting only lung cells with the limitation to protect them from Corona viruses.
- ASLR – In essence, ASLR is a protection mechanism that works by preventing malicious code from finding the resources it needs to perform its operation (by randomizing where said resources are in the process memory). What if we could selectively deprive, or reallocate, access within specific cells to resources that are critical for the virus’ life cycle? This could potentially stop the virus or at least slow its spread down. Like with ASLR, this technique depends on striking a fine balance between affecting the virus and affecting the cell.
- Containers / Process isolation – In cybersec containers create a separate blank unified space for a running application or process, thus isolating it from affecting and being affected by other applications. Biological cells have the cell membrane that acts as a basic isolation barrier. Being basic, it might be better compared to a process memory space than to a security container. Imagine adding another layer of protection over cells, over a group of cells, or perhaps even full organs. This layer can be a chemical one (such as being explored with Zinc), or an organic one, with bacteria, for example, being engineered to act as a buffer (for viruses and not oxygen) for at-risk cells (such as lung cells in the case of Coronavirus).
- VPNs and trusted networking – Applying the cybersec “weakest-link” principle, information security officers often start by limiting access to their networks to only trusted and verified parties. This was quickly expanded to parties that meet security standards and pass security checks. What if we could apply similar standards for people to access specific areas (streets, schools, offices)? For instance, access would be allowed only to people that have been vaccinated or have the right antibodies. Among the listed options this one seems to currently be the most attainable, as it requires the least amount of technological innovation. Yet, the implications to both culture and democracy would be earth-shattering. We can already see initial aspects of such policies being implemented in China in face of the COVID-19 pandemic.
Software security: a road map for bio-engineering
While many of the methods here appear as science fiction when translated from the software to the biological world, some of them are within reach and can conceptually turn the tides of battle in humanity’s favor in this long, ever-escalating, war. Personally, I believe that smart medical wearables and IoT, medical honeypot alarm systems, and area-access regulation based on trusted data are inevitable if the situation (with COVID-19, or other pathogens) continues to escalate.
I believe this thought experiment shows that while translation might not be easy, there is a lot of potential to be had in the discussion and by generally trying to apply cross-pollination between the fields. Software engineering and cybersecurity are fields leading a significant percentage of society’s technological innovation. As leaders, we engineers have the responsibility of looking at the bigger picture, of thinking outside the box, and seeing how we can harness our efforts for the greater good and not just within our own field.