Rookout is the #1 debugging platform for Fortune 500 companies and regulated industries
Certifiably Safe
Rookout is regularly going through security audits and is compliant with many international laws and regulations. We are ISO 27001 and SOC 2 Type 2 audited and GDPR, HIPAA, and CCPA compliant. Our policies are maintained, updated, and communicated regularly as part of our security awareness program.
Rookout activity, actions and changes are logged and can be audited.

Most common security topics we hear our customers ask about
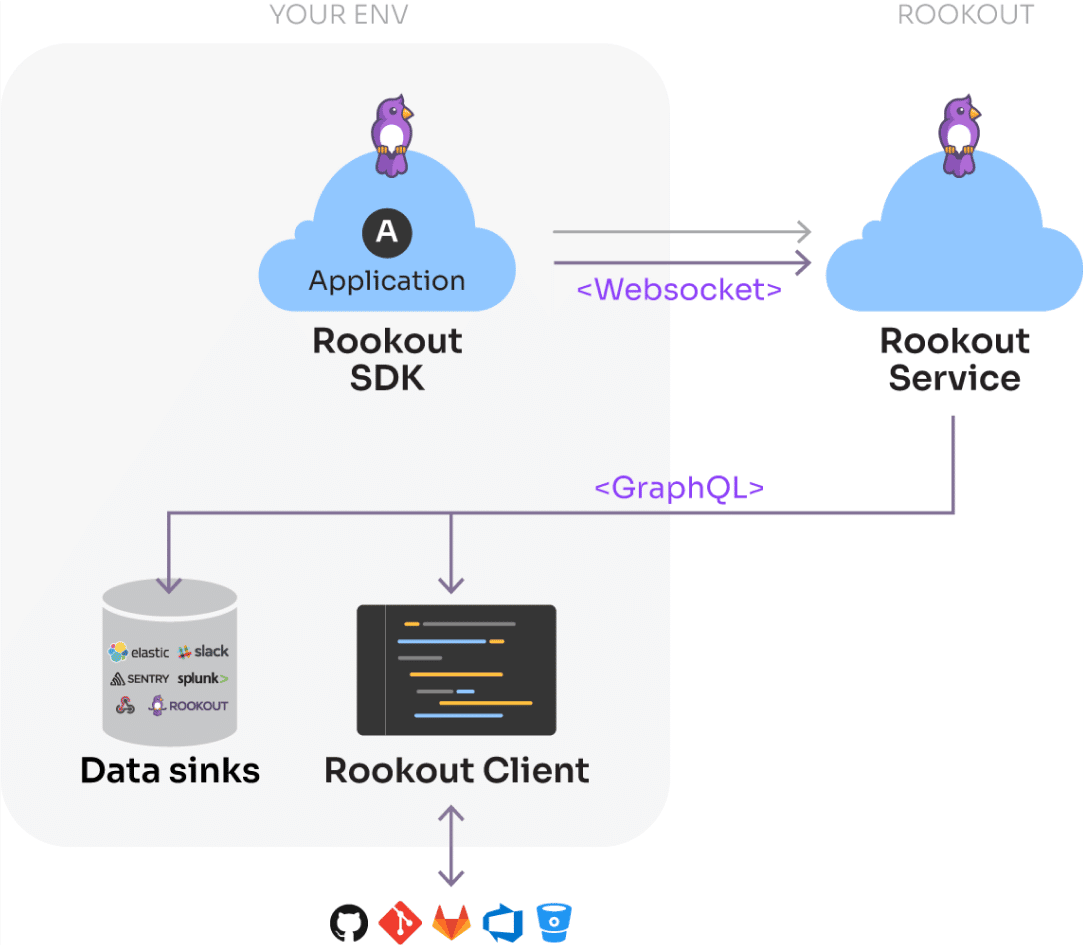
The source code is loaded either from your desktop, or from your favorite source control management service (e.g. GitHub), directly to your browser. Your code is never going through Rookout’s servers, and it cannot be changed from the Rookout Web IDE.
When using traditional remote debugging methods, you must open inbound port to the application so the debugger can access it. This presents security risks, as unwanted applications may access your service. With Rookout, all communication with the Rookout service is outbound using the industry’s security best practices.
Using Rookout you are secure and protected, thanks to:
- A secured and encrypted TLS connection
- The Rookout SDK initiates the connection using outbound communication, therefore the app isn’t exposed to connections from the outside
- A unique Token is used to add another layer of security for the applicative communication channels
- Rookout stores the collected data securely under strict access controls for less than a week
- When the Rookout Hybrid deployment method (aka Data On-Prem) is used, the collected data is cached in-memory within your environment.
Rookout has advanced data redaction capabilities for both include and exclude rule lists, minimizing any risk of PII exposure.
No. By design, the Rookout SDK can-not execute code. Rookout only observes the state of your application (variables and stack trace), and does not change them.
Yes, of course it is.
Rookout is highly committed to information security management and is therefore both regularly audited and compliant with security regulations.
- Rookout is regularly audited for SOC 2 Type 2 compliance and ISO 27001 certification.
- Rookout is compliant and regularly audited for GDPR, CCPA, and HIPAA.
- We are wholly committed to providing the highest security standards and the protection of customer data.
- All Rookout users can mask or filter personal data before any customer data is submitted to our subscription services.
- Rookout keeps up to date with new security and compliance standards and aims to push our standards to the industry’s leading practices.

By using the Rookout hybrid architecture you avoid Rookout processing any of your application data and do not have to report Rookout as a sub-processor.
Yes, Rookout passes Penetration testing and cyber security vulnerability scans for every release and on a regular basis.
Rookout is the #1 debugging platform for Fortune 500 companies and regulated industries
- Data Protection
- Compliance and Privacy
- Security
Access Control
Users may log in to Rookout using their identity provider (IdP), leveraging Rookout’s support for SSO integrations such as SAML, OpenID, and Azure Active Directory. Rookout offers advanced user management features such as just-in-time provisioning and automatic profile updates.
Rookout utilizes a fully-fledged RBAC paradigm, defining what actions each user is entitled to carry out and to which applications they have access. Customers manage roles through their IdP, the Rookout platform, or APIs.
All user actions are audited and may be exported to the customer’s SIEM/SOC.
User settings are configured, hardened, and enforced on a per-tenant basis.
Source Code
Rookout integrates with source control management systems to display the correct source code revision and provide a seamless debugging experience. The process was designed from the ground up to protect source code security and follows the best practices provided by the relevant vendors.
Source code is loaded only on the engineers’ workstation, using the engineers’ privileges. At no point do the Rookout servers access, process, or store customer source code.
Customer Data
All data submitted to the Rookout platform is considered confidential and never leaves the production environment except in limited circumstances, such as supporting a customer request. Data is tagged with the tenant id on ingestion, and strict access controls are enforced for all data access. No application data is retained for longer than a week.
When using the Hybrid Architecture, no application data leaves the customer’s network.
Encrypted Communication
All traffic across public networks is carried out over TLS (enforcing v1.2+ as applicable) and is authenticated on both sides.
All data managed by the Rookout platform is encrypted at rest using multiple layers of AES. Customer-managed keys (CMK) are available upon request.
Compliance
Rookout holds the SOC 2 Type 2 certification for the pillars of Security, Confidentially, Availability, and Privacy, and the ISO27001 certification.
Privacy
Rookout offers Data Processing Agreements (DPAs) for GDPR and CCPA, as well as Business Associate Agreements (BAAs) for HIPAA.
Data Redaction
Rookout includes data redaction controls to purge sensitive data at the source.
Product security
Product security is of paramount importance at Rookout. Rookout has security deeply integrated into its software development lifecycle (SDLC) with controls such as Software Composition Analysis, Static and Dynamic Application Security Testing, Security Design, and Implementation Reviews. In addition, our production environments use hardened base images and configurations alongside security tools such as Firewalls, IDS/IPS, anti-DoS, and more.
Physical security
Rookout production infrastructure is located in a cloud service provider environment. Production access is restricted to authorized Rookout personnel who undergo specific training and is enabled securely through SSO and MFA.
Corporate security
Rookout has deployed strict security and controls for all endpoints and personnel. Rookout conducts regular privacy and security training for all employees and requires the use of security best practices (SSO, MFA, RBAC, etc.). In addition, Rookout regularly undergoes penetration testing and security audits by clients and third-party vendors.